Securing Data at Rest and in Transit to prevent data breach and breaking company systems (500 words)
Public Key infrastructure
Public Key infrastructure will consist of policies needed to manage encryption, distribute public certificates, and securing data. It helps to identify the users and distribute the keys to them. Through that, it will allow individuals to exchange data over the network without thinking about security since the parties they are communicating with are verified.
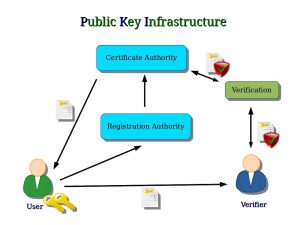
The user sends a key to a third-party verifier who will verify and use the security authority to send a secure key to the user to access the files and the system.
Requirements.
Some of the requirements in securing data include:
- User Authentication and privacy: The certification Authority should identify the users who want or are using the system at any time.
- Ease of use: It should be easy for those managing the PKI, and its integration with other services should be well defined.
- A trusted Certificate Authority: A trusted CA should exist to ensure users do not create fake certificates and the key used to verify a transaction belongs to the person who signed the transaction.
- Certification Revocation List: When a private key is compromised, it should be replaced and blacklisted to avoid any security compromise on the certificates.
Proposed Solutions.
- The users should be registered and, from time to time, checked to monitor their activity to identify any malicious activity in the network.
- The verifier will always authorize the users and check the certificates for any malicious activities.
- The verifier will do the certificate authority in securing data.
Justification.
Having a public Key Infrastructure will help identify the network users and distinguish between the faculty, students, and visitors. It will also help verify the users and the type of data they can access, i.e., students and visitors should not be allowed to access sensitive data on the network. Using PKI will help improve the security of the system and data and prevent any compromise. It is an important component to enhance security since communication between two parties will be secure. PKI can be implemented to secure emails, websites, remote access authentication, encrypt file systems, and securing data.
Secure Protocol Implementation.
A security protocol is vital to determine the data and network security. Security protocols are used to prevent any service, user, or application from accessing the network and hence the data. The network is protected through encryption, and decryption can only be done through a special algorithm.
Requirements.
- Identification: The security protocols to be used should be identified, and this is through testing.
- Security properties: The protocols need to consider essential aspects such as session id and nonce.
- The protocols should have multiple roles in the system design and implementation in securing data.
- Security functions: There should be predefined rules that will help to guide the role of each user and stakeholder in the system. In case of a breach, the functions should provide a way to deal with it.
Proposed Solutions.
- The best security protocol should be identified, which includes the SSL protocol.
- Rules should be set to define the roles of each party in securing data.
- The protocol should be tested through penetration testing to identify any vulnerability.
Justification.
A security protocol to be used in securing data and company IT resources. Testing will then be done to ensure that all the vulnerabilities are addressed before the faculty, students, and visitors access the network. The protocols should have multiple roles to avoid using many security protocols. Standards and rules should also be set to guide the network administrator on what to do if anything happens in the network. Some of the security protocols that can be used on the network include Secure Socket Layer (SSL), Secure Hypertext Transfer Protocol (HTTPS), and Secure File Transfer Protocol (SFTP). SSL, for instance, secures the connection between the users and servers on the network. Therefore, no third party can be allowed to access the communication without being identified and authenticated.
File Encryption to securing data.
Encrypting files will be important to prevent any intruder from accessing files in the network. When data is encrypted, a user cannot read it and will require the verification of the network administrator, who will send the key for them to access it.
Requirements.
- Identification of encryption Algorithms.
- Creating standards on file encryption use.
- Roles on who will provide system authorization.
Proposed Solutions.
- Encryption algorithms such as AES and 3DES should be implemented.
- Users can access some defined data and keys to decrypt the files issued by the administrator.
- Standards should be available to guide the network administrator on what to do if an intruder has accessed data.
- Managing the keys for encrypting files should be handled by the administrator.
- Users should have a guideline on how they can encrypt or decrypt data, and securing data.
Justification.
The two encryption algorithms help provide an extra layer of security in securing data. It takes approximately a million years to break the keys; hence they are the best to encrypt files. The network admin should be responsible for maintaining the key and providing authorization to all the users. Data should also be arranged at different levels, such as the faculty can access a specific type of data that a visitor cannot access. It will help protect the data on the network, and if an intruder has access to the data, they will not be able to access the data due to the encryption provided. For instance, when the data is encrypted using AES, it will have encryption and decryption keys. For any user to read it, they must request the keys from the administrator, who will then verify and give access to the users. The benefit of file encryption is that it takes millions of years for one to crack the key; hence even when the intruder has access to the data, they will not be able to decrypt it will be secure.
Hashing.
Hashing can be used to store all the passwords of the users, and help in securing data. Hashing can store passwords, search the database, and verify files. Hashing allows one to use most file types such as texts, documents, and MP3 files. The algorithm to be used should have more hash values to give more bits of data and prevent any collision from taking place.
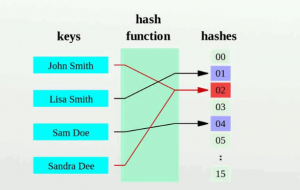
Requirements.
- The type of hash functions to be used.
- How hashing should be done.
Proposed Solutions.
- All passwords, files, and documents should be hashed, to help in securing data.
- The admin should have keys for the hash functions.
- Algorithms such as MD5, SHA, and SHA2 can be used to hash the data.
Justification.
Hashing all passwords, files, and documents will help make an intruder unable to verify the content of the data since they are arranged differently. The admin should implement the hashing algorithms and ensure it is securely stored in the database. Hashing will provide authentication and authenticity of the data. The benefit of using hashing is that all the results of the hashes have the same length despite having different sizes hence making it hard for an intruder to establish the content of the data. SHA 256 bits should be used as it is more secure and verified to provide the best hashes for all types of data.
Backup and Restore.
Data on the network used by the faculty, student, and visitors should be backed up securely. The role of backing up the data should be assigned to specific people. At the same time, the network administrator should be responsible for verifying the data and providing access to the user to restore data when called upon. The server room should be restricted to specific people, and the data stored in the server should be encrypted. A timeframe should be designed on when data should be backed up.
Requirements.
- The location of the server room should be identified in securing data.
- Physical security measures should be used for the server room in securing data.
- The period for data backup should be set.
- Rules should be put in place on when to restore data.
- Data stored on the database should be encrypted to provide an extra layer of security.
Proposed Solutions.
- The server’s physical location should be restricted to the network administrator only.
- A period should be set when data should be backed up to guarantee security of data.
- The administrator should check the data backed up.
- AES encryption algorithm should be used to encrypt data stored in the database.
Justification.
Preventing access to the server room will help prevent any intruder from accessing the data. A schedule should be created on when data should be backed up and who will perform the operation and securing data. The administrator should verify to avoid uploading malware to the servers. By using these proposed solutions, the security of the data will be guaranteed. Measures should also be put in place to guide the administrator on what to do in case of a security breach. A distributed backup should be created to allow users to back up their data on the database. For recovery, that should be an audit trail that will help record all the recent transactions done by the users and help establish any malicious activity. Backing up of data should also be simple, efficient, and not time-consuming. Backing up should also be a full backup to avoid omitting any data when backing up.



