How do you utilize risk assessment methodology in developing an excellent research paper? 700 words
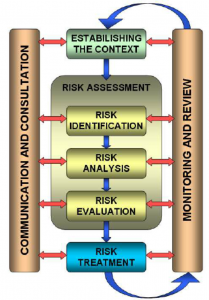
Risk Assessment Methodology
I will employ to use a qualitative risk assessment methodology for Case study 1. I will also use the five why’s analysis technique to better understand the risks I will be dealing with. The risk assessment will help to guide all the management decisions that will be made in the Navy.
The effects of the risk can be data loss, processes interruption, loss of lives, or personnel. The consequences of the risk will be employee turnover, organization brand damage, and high costs of repair and legal fees.
Planning.
It will be the first step of risk assessment. Using the qualitative risk assessment methodology will help me identify the probability of the risk occurring and its impact on the organization. Panning will help identify the resources required to carry out the assessment, the communication process and the team, and the duties of each individual.
Identification of hazards.
It is the second step of the risk assessment. Hazards will be identified by conducting interviews with the employees, doing a physical assessment, brainstorming, and reviewing data such as incidents that have taken place in the past. The biggest hazard in our case is the structure and mode of operation of the organization. Being a government institution, the navy handles very critical information, and it can be a target from international enemies. Rotations of employees make some of the critical sectors, such as the security of servers and database management systems, vulnerable.
- Risks analysis.
It is the third step of the risk assessment. Each process should be analyzed in this step, and the consequence of an attack given. It will help to identify the critical processes and establish ways that can be used to prevent the risk. Through staff rotation, some of the critical sectors will be handled by inexperienced staff. In this case, intruders will have an easy time accessing the systems and data, which will heavily affect the organization’s operations. The maintenance and security of the database should be left for the experienced staff, and they should not be rotated. All the data handled by the navy should be backed up frequently. Inspection should also be done to ensure the data backed up is intended and only the authorized personnel have access to the database.
Risk evaluation.
It is the fourth step of the risk assessment. These three parameters should be used to evaluate the risks; exposure, probability, severity. Once the evaluation is done, the following hierarchy of control can be used to identify ways to eliminate the risk.
- Elimination.
In critical sectors, the staff should not be rotated, and only the experienced staff should handle those processes. Human factors heavily put the organization at risk of threats from hackers. Data should always be backed up in several servers so that in case the main server is attacked, the others will be used, and no process in the organization will be affected.
- Changing work methods.
The system should be automated to signal to the administrator if there is a breach. Measures should also be put in place to state what should be done if there is a security breach.
- Isolation.
Only a few authorized personnel should access the server room. The data in the database should also be encrypted. Encrypting the data with encryption algorithms such as AES and 3DES will help ensure that the data will always be secure even when the organization is attacked and the data stolen.
- Administrative control.
The management in the navy should ensure that they establish who are the process owners and the roles they each have. A record should always be kept on what was backed up, by who, and the time. Frequent training should be done to help the employees establish what they may face and how to handle different situations based on the changing times. Auditing should also be done to help establish the effectiveness of processes in the organization.
Considering the risk’s impact on the organization, the risk assessment should be a continuous process. All the processes should be able to communicate, and new ways should always be established on how to monitor and control the risk in the navy.



